My Journey with DMARC: A Lesson Learned in Email Authentication

When it comes to email security, understanding how different email authentication protocols work together can be confusing. Recently, I found myself deep in the weeds of a DMARC implementation for a customer. During this process, I incorrectly assumed that both Sender Policy Framework (SPF) and DomainKeys Identified Mail (DKIM) had to align for an email to pass DMARC checks. In this blog post, I will share my experience and what I learned about these protocols, their roles in email security, and how DMARC truly functions.
Understanding the Basics: SPF, DKIM, and DMARC
Before diving into my specific experience, it’s essential to understand the three main protocols used in email authentication: SPF, DKIM, and DMARC.
- SPF (Sender Policy Framework): SPF is an email authentication protocol that allows domain owners to specify which IP addresses are allowed to send emails on their behalf. It works by adding a special SPF record to the domain’s DNS settings. When an email is received, the receiving server checks the email’s sender IP address against the SPF record. If the IP address is listed in the SPF record, the email passes SPF; otherwise, it fails. However, SPF does not guarantee that the sender’s domain has not been spoofed.
- DKIM (DomainKeys Identified Mail): DKIM provides a way to check that an email was indeed sent and authorized by the owner of that domain. This is done through a cryptographic signature. The sender’s server signs the email with a private key, and the receiving server verifies it using a public key published in the domain’s DNS records. If the signature matches, it means the email has not been tampered with and is indeed from the stated sender.
- DMARC (Domain-based Message Authentication, Reporting, and Conformance): DMARC builds on SPF and DKIM by providing a way for domain owners to specify what happens if an email fails SPF or DKIM checks. Domain owners publish DMARC policies in their DNS records, indicating whether to accept, quarantine, or reject emails that fail these checks. Additionally, DMARC provides a reporting mechanism that allows domain owners to receive feedback on email authentication activity.
The Assumption: SPF and DKIM Must Both Align for DMARC to Pass
While setting up DMARC for a customer domain, I initially assumed that for an email to pass DMARC, both SPF and DKIM must align. This seemed logical to me; if DMARC builds on SPF and DKIM, wouldn’t it make sense that both need to align for maximum security?
However, after reviewing the DMARC reports, I quickly discovered that this assumption was incorrect. DMARC does not require both SPF and DKIM to align. Instead, it requires either SPF or DKIM to align for an email to pass DMARC checks.
How DMARC Actually Works
Here’s how DMARC functions in practice:
- Alignment Requirement: DMARC requires either SPF or DKIM to align with the “From” address in an email. “Alignment” means that the domain in the “From” address matches the domain in the SPF or DKIM records. This is where I misunderstood DMARC’s functionality. While both SPF and DKIM provide methods to verify the authenticity of an email, DMARC only needs one of these methods to succeed for an email to be considered authentic.
- DMARC Policy Actions: When an email fails both SPF and DKIM checks, the DMARC policy specifies what to do with that email. There are three main DMARC policy actions:
- none: No specific action is taken, but reports are still generated.
- quarantine: The email is treated as suspicious and may be sent to spam or junk folders.
- reject: The email is outright rejected, and the receiving server does not deliver it to the recipient.
- DMARC Reports: One of the valuable features of DMARC is its reporting mechanism. DMARC provides two types of reports:
- Aggregate Reports: These provide a summary of email authentication results, giving insights into how many emails passed or failed DMARC checks.
- Forensic Reports: These provide detailed information about each individual email that failed DMARC checks, helping domain owners diagnose specific issues.
Realizing the Mistake: The Role of SPF and DKIM
During the DMARC implementation, I noticed that some legitimate emails were being delivered even though they were failing on DKIM but passing on SPF:
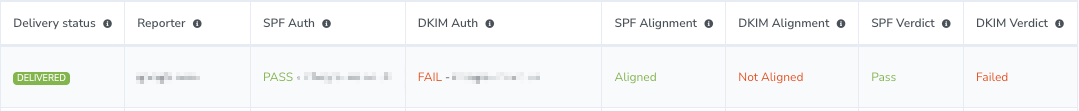
This was because I was under the impression that both SPF and DKIM had to align. Upon further investigation and research, I learned that DMARC policy allows for either SPF or DKIM to pass.
If an email passes SPF checks and aligns with the “From” domain but fails DKIM checks, it will still pass DMARC, and vice versa. This flexibility is vital for various use cases where one authentication method might not be feasible or reliable, depending on the email flow or third-party services used.
Another Assumption Regarding SPF and DMARC...
Historically, I was always told that you should configure your SPF record to be a hard fail (uses -all) rather than a soft fail (uses ~all) as a security best practice. However, when DMARC has been implemented, then this is probably the exception to the case.
Below is a blog post from RED SIFT that explains this:

TL;DR...
-all can cause an immediate rejection causing the message to be rejected before any DMARC processing takes place. ~all in combination with DMARC and DKIM will still reject mail if SPF and DKIM fail. It is therefore recommended to use ~all if using DKIM and DMARC authentication.
Conclusion
Email authentication protocols like SPF, DKIM, and DMARC are essential tools for protecting your domain from phishing and spoofing attacks. However, it’s crucial to understand how these protocols interact and the flexibility they provide. DMARC’s design, which requires only one of SPF or DKIM to align, provides a balanced approach to email security without overly restricting legitimate email flows.
My experience taught me the importance of reading the fine details and not making assumptions about how security protocols work. With the right understanding and proper configuration, you can effectively use DMARC to protect your domain and ensure your emails reach their intended recipients safely.
