Azure Arc - Deploy MDE Extension via Script

In this post, if you had to take a shot for every time you read the word "Defender", I think you would need to visit a hospital...!
The other day, I was faced with a challenge for enrolling some Azure Arc Servers with the MDE.Windows extension so they can have the Defender for Endpoint installed onto them. Stepping back from this, the customer in question had started to onboard their on-premises server estate to Azure Arc as they are using Arc for sending logs to Azure Sentinel, and they have some custom data collection rules. We have created a separate subscription for onboarding the Azure Arc resources and segregating them by resource type. E.g. resource group for domain controllers, web servers, RDS etc.
The customer didn't want to blanket enable Defender for Endpoint in the Defender for Cloud console as part of the Defender for Servers deployment (jeez, that is a lot of mentions for Defender 🛡️!!). This was mainly because they were looking to migrate from another virus provider to Defender for Endpoint but didn't want to take the big bang approach, and they didn't want to enable Defender for Endpoint on the existing Azure Arc workloads.
The challenge is that Defender for Servers and Defender for Endpoint is controlled at the subscription level within Azure. Therefore when you enable Defender for Servers, it applies to ALL resources in that subscription. (Please, come on Microsoft, if we can control this at the Resource Group level, that would be awesome!). So we thought, why don't we move the resources we have already onboarded to another subscription and we can then continue with the Arc onboarded with Defender for Servers. Ha, well that wasn't possible in our case due to having the custom Data Collection Rules, as it screwed up the rules when you move the Arc resource, and you have to recreate them from scratch!
So here is what we did...
In our Azure Arc subscription, we enabled Defender for Servers P1 but disabled the Endpoint Protection to ensure the Azure Arc agent would not install the MDE.Windows extension (which is the Defender for Endpoint installer).
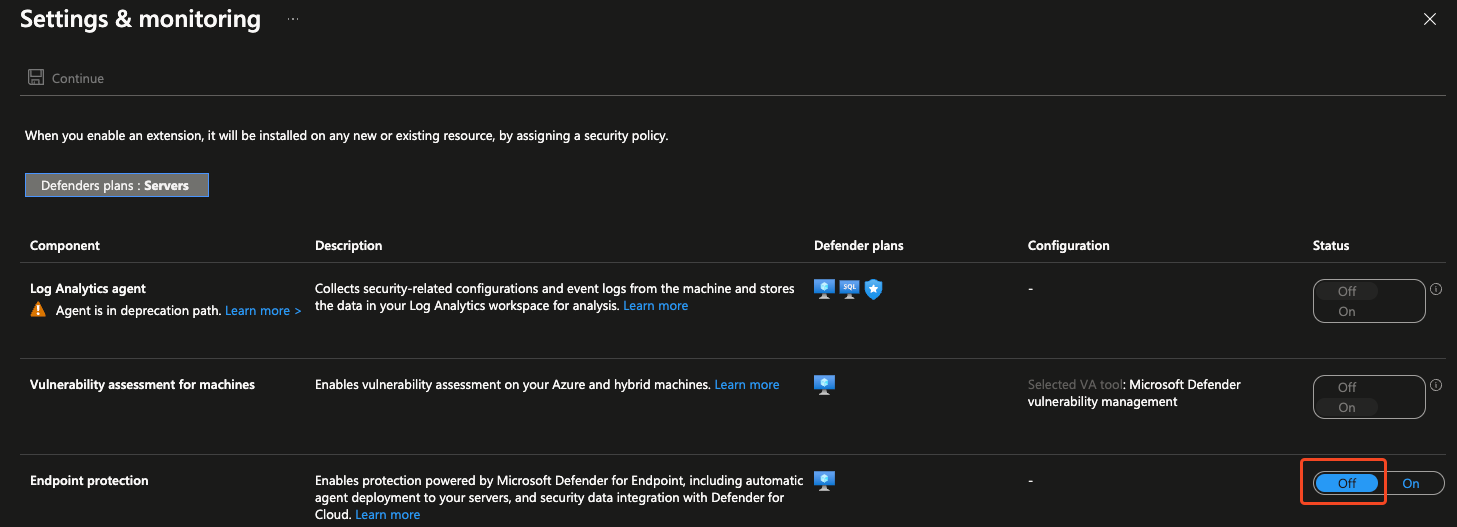
You can then run a PowerShell script against the Azure Arc VM. I utilised the Azure Cloud Shell to run the below script:
$vm = Get-AzConnectedMachine -ResourceGroupName "RG-Name" -Name "VM-Name"
$mdePackage = Invoke-AzRestMethod -Uri https://management.azure.com/subscriptions/$($vm.id.split('/')[2])/providers/Microsoft.Security/mdeOnboardings/?api-version=2021-10-01-preview
$protectedSetting = @{
"defenderForEndpointOnboardingScript" = ($mdePackage.content | ConvertFrom-Json).value.properties.onboardingPackageWindows
}
$Setting = @{
"azureResourceId" = $vm.Id
"vNextEnabled" = $true
}
New-AzConnectedMachineExtension -Name 'MDE.Windows' -ExtensionType 'MDE.Windows' -ResourceGroupName $vm.ResourceGroupName -MachineName $vm.Name -Location $vm.Location -Publisher 'Microsoft.Azure.AzureDefenderForServers' -Settings $Setting -ProtectedSetting $protectedSetting -AutoUpgradeMinorVersion -TypeHandlerVersion '1.0'After running this script, you should then see the following within the extension section of the Azure Arc VM:
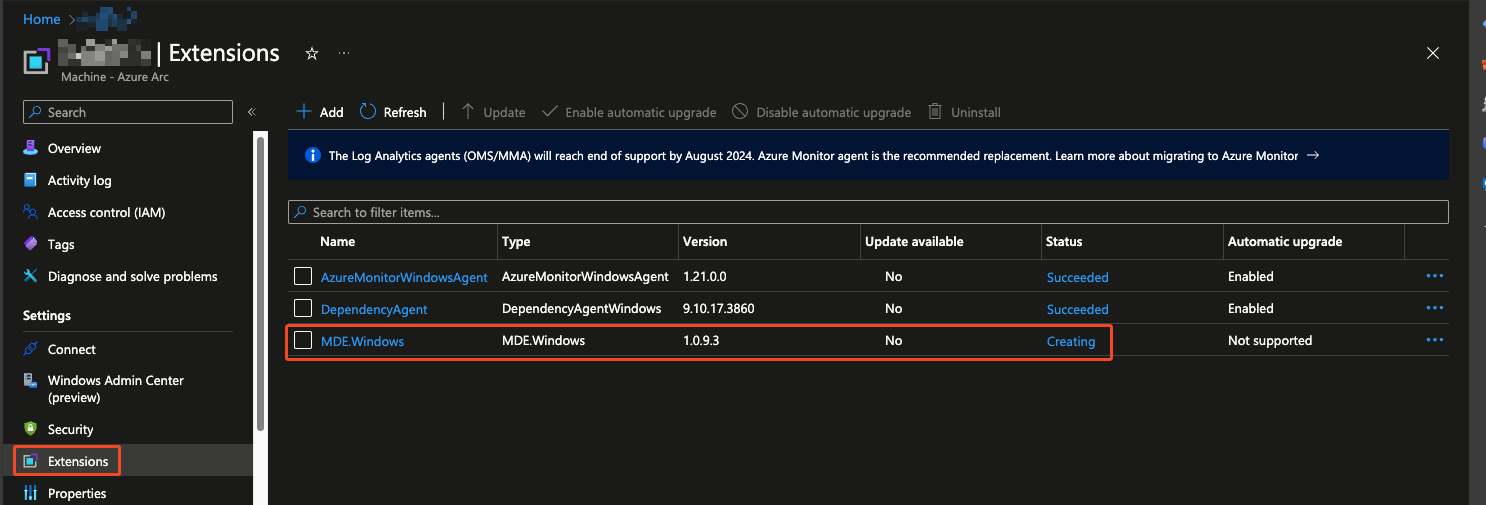
It will take several minutes to complete, after which it will say succeeded:
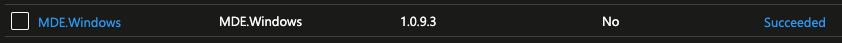
The VM should now have Defender for Endpoint installed!
Also, if you want to dig into the logs of the installer, I recommend checking out these log paths, as they also helped me with some installation failures relating to the proxy:
- C:\ProgramData\GuestConfig\extension_logs\Microsoft.Azure.AzureDefenderForServers.MDE.Windows
- C:\ProgramData\GuestConfig\ext_mgr_logs
In conclusion, it was a bit of a pain to get this working to onboard some servers to Defender for Endpoint using the Arc agent, but we did get it working using the above script. Once we had verified the Defender for Endpoint configuration and that it wasn't going to break anything, we deployed it to the other 25 resources in the Arc subscription, after which we enabled the Defender for Endpoint option with Defender for Servers in the Defender for Cloud blade for that subscription.
And.... if you have been taking a shot of whisky every time you have read the word "Defender" and are still standing, then I applaud you 👏